Portal, AZ - Rodeo, NM
Serving The Communities Of Portal and Rodeo (www.portal-rodeo.com)
Serving The Communities Of Portal and Rodeo (www.portal-rodeo.com)

Protect Your Computer - Malware-Ransomware

Ransomware: Should You Be Losing Sleep Over This Computer Version Of A Pandemic?
Hi everyone. First it’s the record-breaking drought. Then comes the Covid pandemic. Now, hardly a day passes when we don’t read or hear about computers being taken over by malicious programs called ransomware. You probably know how it works: your computer is frozen and your files encrypted. Returning everything to normal will cost you big bucks. Why does it infect you? Because you probably answered an e-mail that looked official and/or visited a web site that also looked legitimate. I have been tempted many times. Just look at the following e-mail I recently received from “Amazon” asking me to add my personal information so I could track a recent order.
To: htopoff@vtc.net
From: shipment-tracing@amazon.com
Looks perfectly normal, right? Except, from experience I know that every other e-mail I got from Amazon (and I get plenty) had the word “tracking” not “tracing.” A typo? NO WAY. I deleted the e-mail and within a few hours I received this e-mail from Amazon:
To: htopoff@vtc.net
From: shipment-tracking@amazon.com
Would YOU have recognized the difference. Probably not.
So, let’s talk about malware and particularly ransomware. According to an article in today’s New York Times, the team that hacked the Colonial Pipeline is starting a franchise of sorts. They are selling information to anyone, about how to set up a ransomware hacking “business.” Here are my ideas about what we all can do to lower the probability that we will become victims.
Q. Would we, in our small communities, really be targets?
Let’s face it. I doubt that Russian (or any) hackers believe that they can squeeze millions of dollars of ransom from the average citizen. They obviously have bigger fish to fry - pipelines, power grids, factories, government agencies, etc. The same story holds for hackers interested in credit card numbers. They can steal yours but, if possible, why not go after Target or Walmart, where they can steal lots of credit card data. Nevertheless, one of my neighbors did shell out $400 because she was told (by telephone) that her computer was “captured.”
Here’s a funny story. I once received a call from India, telling me that my PC was hacked and they would fix it for a fee. I told them I had a Mac. The caller said, “Oh, let me transfer you to a Mac specialist." After a brief silence, the SAME person came back to the phone and told me my Mac was hacked and they would fix it for a fee. I told them that my Mac was turned off. “But was it plugged into a wall outlet,” he asked. Yes indeed. Then he said that my Mac was hacked through the electrical grid. I hung up, laughing. Problem is, do you realize how many people would actually believe such a story? Plenty, I’m sure.
Q. OK. How can I protect my computer from becoming infiltrated by ransomware? Let me count the ways!
Software (Apps): The best ransomware protection software will be able to prevent ransomware not just infecting your computers, but also prevent it from being able to change your files and folders. Most of the best antivirus software and anti-malware software will have protections against ransomware built in.
If you are on a budget (or have NO budget) check out this highly rated but FREE app. I know, the name sounds Russian, but you can trust this one!
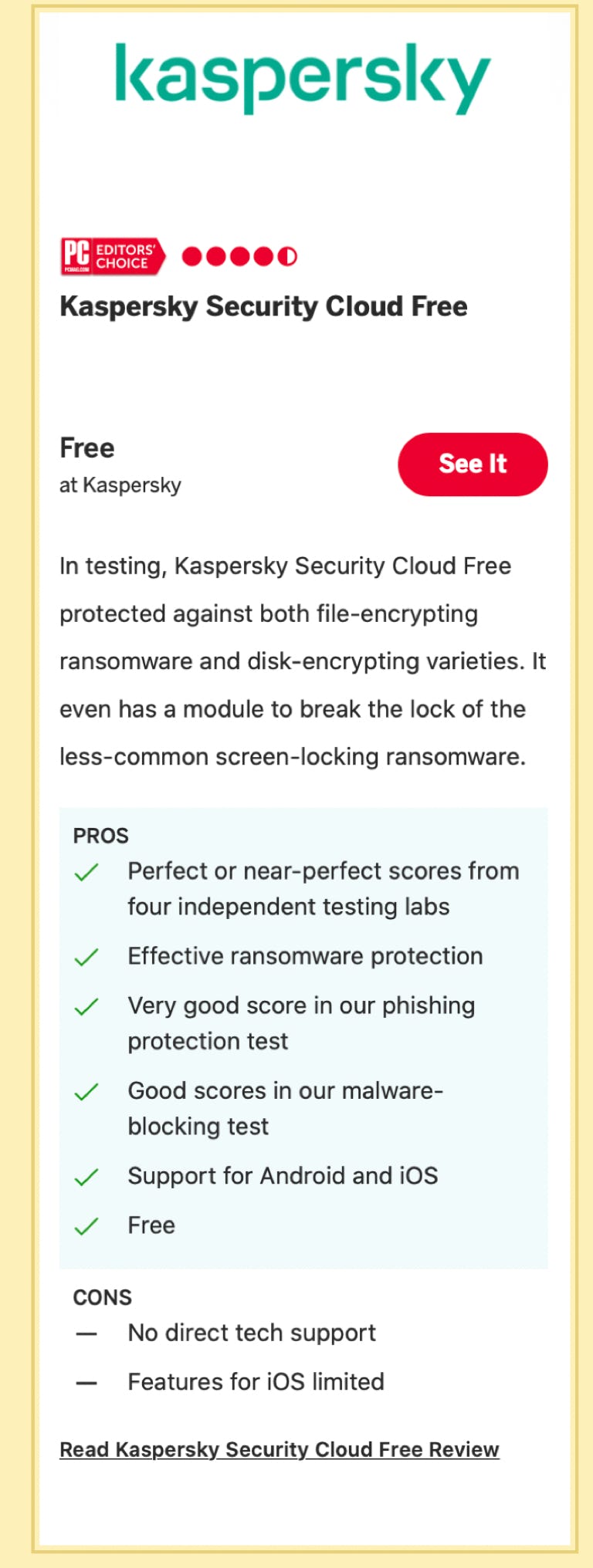
Most Anti-Ransomware Apps do have a cost. Some, you can purchase outright. Others charge a monthly or annual fee. Choose a service that includes periodic updates as viruses (both Coronavirus and Computer Viruses) keep changing.
Here is a web site that compares the most highly rated Apps.
https://www.pcmag.com/picks/the-best-ransomware-protection
Q. Is there anything I can do on my computer, with an App?
You bet. First (and foremost), be vigilant about your e-mails and web sites. Check this out:
For example, I get an e-mail from Publishers Warehouse. It looks like this:

So, I move my mouse onto the e-mail address and it turns blue:
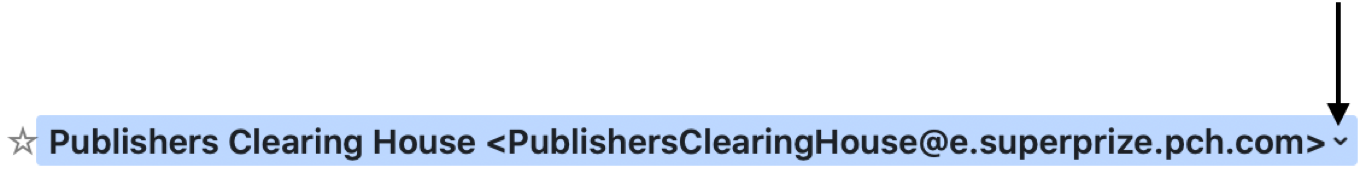
See that little “v” that appears at the end. Click on that and see what appears.
Make sure the gray area matches the blue. If it doesn’t, or has all manner of extraneous characters, don’t respond to the e-mail. Delete it!

I know this sounds like a lot of work. Clearly, you don’t have to do this for every e-mail you receive. Just focus on e-mails that you receive for the first time and you are not familiar with the sender. Don’t be paranoid, just cautious!
The same common sense holds for web sites. We all get notices directing us to all manner of web sites, so how are we to know which are suspicious. The operating systems of Windows and Mac computers have pretty good built in warning systems, but these will work ONLY if you keep your operating system up to date. I know that many people never update their operating system because they are afraid it will screw up their computer, or add new features that that don’t want or need. Just remember that EVERY operating system update includes better and stronger security features.
Q. Couldn’t I just make a backup of my files so, if my computer is compromised, I can just erase everything and load it up from the backup.
Sure, but even with this method there is lots to know. Not difficult, just lots.
First comes the on-line back up apps: Drop Box, Amazon, Google, iCloud, Carbonite, and lots of others. All will give you free storage for a limited amount of data. Backing up a full computer (read “tons” of photos and music, in addition to data) will cost (again monthly or annually), depending on the size of all your files.
If you have a Mac, iCloud is a no-brainer. Drop Box, Amazon, Google are very well known. Of the private, dedicated companies, Blackblaze is one of the most often cited. But there are soooo many - here is list of 21 sites.
https://www.lifewire.com/online-backup-services-reviewed-2624712
Q. What about backing up to an external hard drive?
A. That’s precisely what I do!! I think it’s the BEST all-around protection.
I have a backup portable hard drive which sits next to my computer. Although Macs come with an App called Time Machine built in, I prefer a better procedure. I purchased (about $25.00) an App called SuperDuper. A similar App is Carbon Copy Cloner. I plug the external drive into my computer and SuperDuper copies everything. Not just data files - the operating system too. In fact, it does what Time Machine cannot do. It turns my external drive into a clone of my computer’s drive. It makes a bootable clone. So, if my hard drive is compromised, just ends its life or if I purchase a new computer. I connect the external drive to my new computer and let SuperDuper put EVERYTHING back. After about 45 minutes, I can turn on my new computer and start working working where I left off.
SuperDuper and Carbon Copy Cloner only work on Mac computers. The Windows equivalent can be found here:
https://www.ubackup.com/articles/superduper-windows-3889.html
A cloned backup is probably the best protection you can have, and can provide complete peace of mind. No matter what happens to your computer - hard drive failure, computer infected with a virus, computer hacked for ransom - you can always erase the hard drive, reformat it, and restore ALL of it from your backup!
Now some people say that backing up to an external drive is dangerous, because if the house burns down, the external drive goes too. I have two answers. Not everyone is computer savvy, and managing an on-line backup may be a bit too daunting. Second, In all the years we have lived in Portal, I have never heard of a house burning to the ground and destroying a computer. I know it could happen, but it would be a rare event indeed. Nevertheless, I solve this problem by having a second external drive that I keep out of the house, in my shed. About once a week I bring it in, hook it up, copy everything and return it to the shed.
Keep this in mind. If you decide to use a backup portable drive, shut it off or disconnect it from your computer when not backing it up. Remember, we are protecting your files from hacking, phishing, malware, ransomware and other destructive software. If your backup drive is off or disconnected, it will remain safe, regardless of what happened to your computer.
Well, that seems like enough for now. If you have other ideas or procedures for protecting your devices from foreign digital threats, please do let me know. I can and will edit this essay to include any information that helps us to stay digitally safe. And if you need any help implementing these features, contact me and I’ll be happy to help.
Your friendly webmeister: Howeird
htopoff@mac.com
520-558 2433